Implementing a Web Application Firewall (WAF) to block malicious traffic involves several key steps: selecting the right WAF solution, deploying it properly, configuring security rules, testing, monitoring, and maintaining it regularly.
-
Evaluation and Planning: Assess your web application infrastructure and security needs. Consider factors like ease of management, scalability, and customization options when selecting a WAF solution.
-
Deployment: Deploy the WAF in front of your web applications, typically as a reverse proxy or inline between the network and the application server. Common deployment modes include:
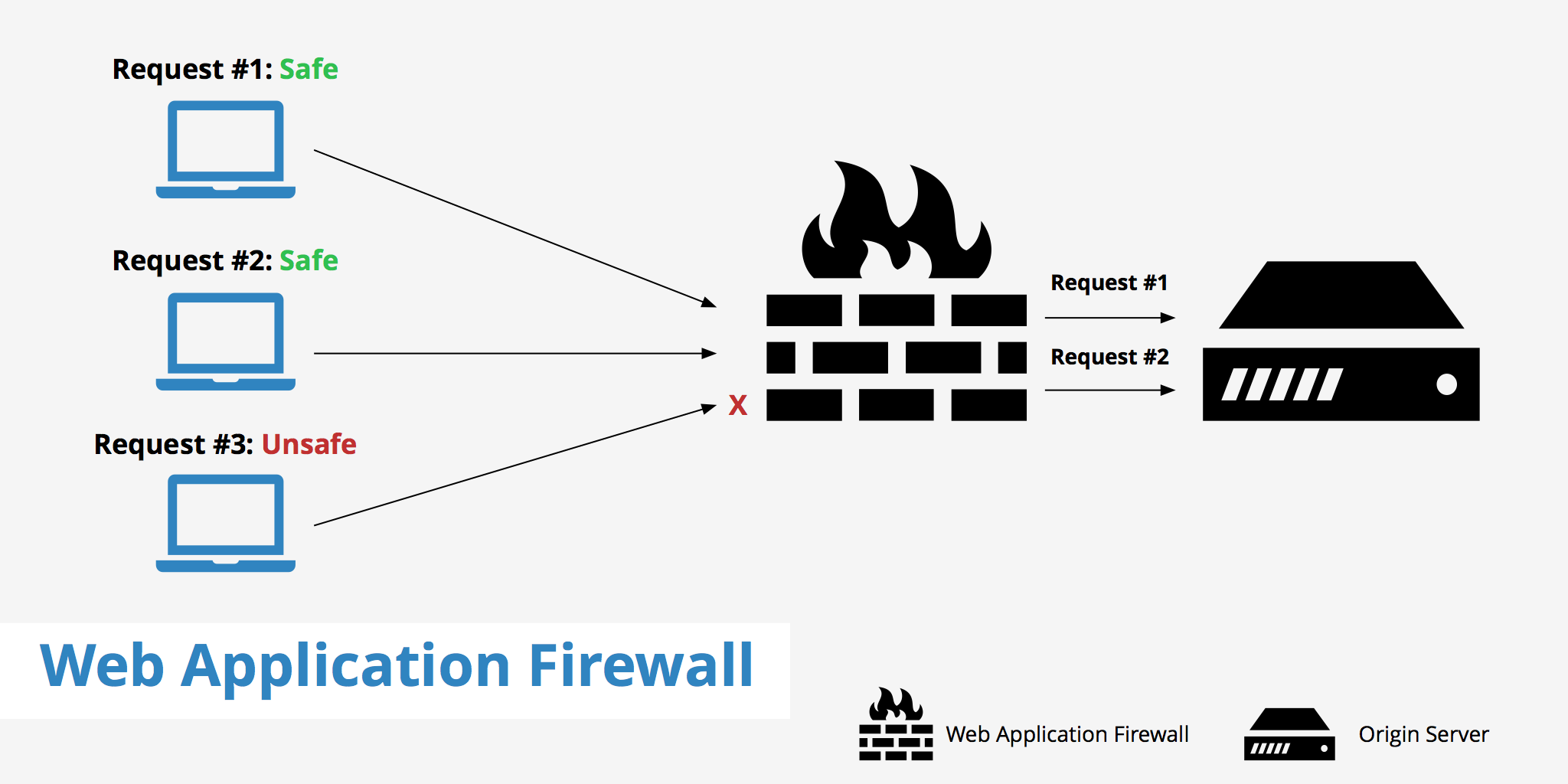
- Inline Mode: Actively intercepts and blocks malicious traffic before it reaches the server.
- Out-of-Band Mode: Monitors traffic passively and alerts on threats without blocking.
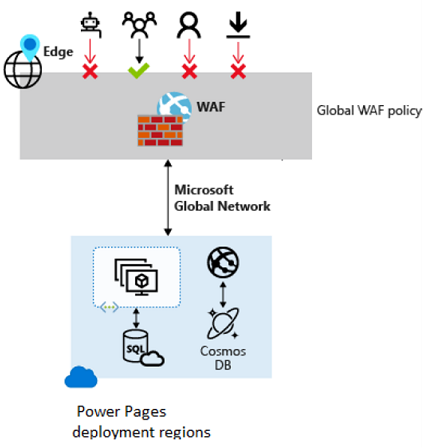
- Cloud-Based: Redirects traffic through a cloud provider’s infrastructure, suitable for scalable cloud applications.
- Appliance-Based: Physical devices installed on-premises for dedicated protection.
-
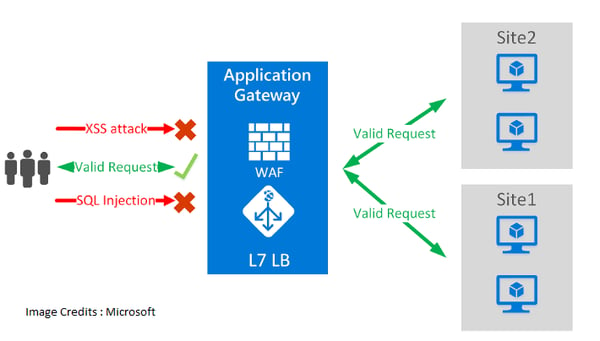
Configuration: Set up the WAF with security policies and rule sets tailored to your application. Rules typically protect against common web vulnerabilities such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and others. You can also configure IP blocking, rate limiting, and payload inspection.
-
Testing and Validation: Use penetration testing tools to verify that the WAF blocks malicious traffic effectively without disrupting legitimate users. Adjust rules as necessary to minimize false positives and negatives.
-
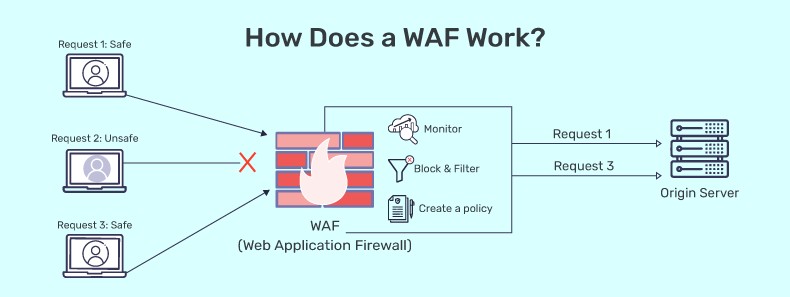
Monitoring and Logging: Enable detailed logging and real-time monitoring to track traffic and security events. Set up alerts for suspicious activities to enable rapid incident response.
-
Regular Updates and Maintenance: Keep the WAF updated with the latest security patches and rule sets to defend against evolving threats. Continuously review and tune configurations based on new vulnerabilities and changes in your web applications.
-
Incident Response: Establish procedures to investigate and mitigate incidents detected by the WAF, ensuring a swift response to security breaches.
Additional technical details:
- WAFs inspect HTTP requests (GET, POST, PUT, DELETE) including headers, query strings, and body content to identify malicious patterns.
- Connection types for WAFs can include DNS-based redirection (CNAME) or transparent proxy modes, depending on your infrastructure and requirements.
By following these steps, a WAF can effectively filter and block malicious traffic, protecting web applications from a wide range of attacks while allowing legitimate traffic to pass through.















Ang PH Ranking ay nag-aalok ng pinakamataas na kalidad ng mga serbisyo sa website traffic sa Pilipinas. Nagbibigay kami ng iba’t ibang uri ng serbisyo sa trapiko para sa aming mga kliyente, kabilang ang website traffic, desktop traffic, mobile traffic, Google traffic, search traffic, eCommerce traffic, YouTube traffic, at TikTok traffic. Ang aming website ay may 100% kasiyahan ng customer, kaya maaari kang bumili ng malaking dami ng SEO traffic online nang may kumpiyansa. Sa halagang 720 PHP bawat buwan, maaari mong agad pataasin ang trapiko sa website, pagandahin ang SEO performance, at pataasin ang iyong mga benta!
Nahihirapan bang pumili ng traffic package? Makipag-ugnayan sa amin, at tutulungan ka ng aming staff.
Libreng Konsultasyon